
If you suspect a hack or suspicious activity on your website, it can be a nerve-wracking experience. Until you know for sure, you cannot determine the reason, nor the solution. Wondering how to remove malware from WordPress site?
Do not worry, we will help you clean malware from WordPress, determine the cause, and save you any future trouble.
The first thing to do now is to scan your website.
A scan will confirm if your website has malware. It is important to know this information because malware attacks can wreak havoc with your WordPress site if not identified in time. Malware can stay hidden on your website and redirect your users, show them indecent content, cut off your access, or even steal confidential information.
This sounds like a nightmare, but there is a solution, and we’re going to show you exactly how to fix this situation by removing malware from WordPress successfully.
TL;DR: Remove malware in minutes from your WordPress website without losing anything. A malware attack can spell disaster for your WordPress website, but we have detailed a step-by-step guide to explain how to remove malware from the WordPress site. Use MalCare for a quick scan and to auto-clean your WordPress website.
How to know if your WordPress site is infected with malware
Identifying malware on your WordPress website is not as easy as it sounds. You may have already noticed something going awry, but the truth is that malware is sneaky, it can hide from the admin very easily and you may be the last person to see issues on your website while your users are noticing redirects and spam.
So how to confirm if your WordPress site is infected with malware?
The best way to confirm is to scan your website. But there are a few symptoms to look out for.
Symptoms of having malware on your WordPress website
When malware infects your website, you may not notice big changes. But there are other ways in which malware will affect your website. This can be noticed through the following symptoms.
Slow load time
Malware often hides malicious code and files on your website. This adds additional data to your website server and overwhelms it, which can lead to your WordPress site loading slower than before. If you notice that your website loading time is significantly higher than it used to be, conduct a scan to make sure that your website is safe.
Unauthorized redirects
If you notice your website redirecting to spam pages, it is one of the most common signs of malware. Hackers use these techniques to get higher inbound visitors to their web pages so that they get a higher placement on search engines.
Blacklisting
Have you ever tried to visit a website and Google throws out a big red warning sign suggesting that this website is not secure to visit?
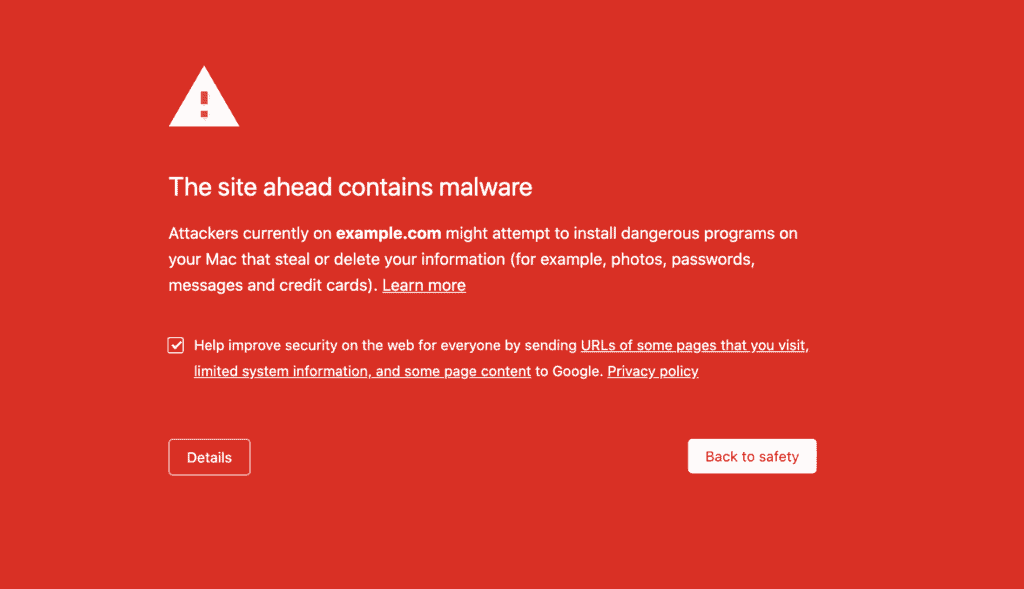
This is known as the Google blacklist, and this list is used by other search engines as well as anti-virus companies to categorize websites as unsafe to visit. Google adds over 10,000 websites to its blacklist every day if it finds malware or suspicious activity on them. As Google uses an evolving algorithm to detect unsafe websites for its users, It is therefore a pretty strong indicator of malware on your WordPress site.
Website defacement
Malware can change how users see your website. Your homepage could turn into an ad for an illegal product, or change to a hacked warning, with a demand from the hackers. Defacement can be very bad for a business and can lead to a decline in brand reputation as well as consumer trust.
Data loss
Malicious code can often corrupt or delete the data on your website. This could be the files and database on your website including confidential information such as customer details, financial credentials, and business information. Data loss is bad in itself, but stringent legal regulations for handling data can make it even worse. You may face lawsuits and fines from authorities if your data is lost or falls into the wrong hands.
Web host account suspension
Your web host has a vested interest in ensuring that all the websites on its servers are clean. This is because an infected site could potentially infect other sites on the server with malware, and the web hosts want to keep malware away from their servers. So if they detect malware on your website, they could suspend your account. If your web host account gets suspended, that is a big sign of malware on your website.
Visitor complaints
Hackers don’t want admin to find malware on their website, as they want to stay on there as long as possible. So they usually hide the malware in places that are not evident to the admin. So even if you don’t notice any symptoms, it is no guarantee that your site is clean. Your visitors still may see certain symptoms, and if you’re fortunate, complain about them to you. Take visitor feedback very seriously as it could be a sign of malware.
Where can you locate malware on your WordPress site
The tricky thing about malware is that it can be located anywhere. Hackers don’t want you to find the malware, so they find increasingly creative ways to hide it on your website. But there are a few typical places where malware is found often.
Common PHP files
Core WordPress files such as index.php, wp-config.php, and wp-load.php which carry common malware through include/require statements. This type of malware is added to PHP files and then loads other malicious code.
Publicly accessible folders
Folders like wp-content/uploads, which are accessible to the public often carry malware. The best way to protect these folders is to add a check that does not allow PHP files as uploads.
Cache folders
Cache folders may still carry malware files after a clean-up, and therefore, hide malware. Make sure to clear your cache after a clean-up.
Root directory folders
Any folder in the root directory or the parent directory, which is not created by you can hide malware. These folders often carry phishing malware, so it is best to clean up these folders at the earliest.
.htaccess
Any config files such as .htaccess are a good place to look out for malware, as these files are often modified by hackers because they are critical to the website.
Important Note: Bear in mind that this list of files and locations is not exhaustive by any means. It is just a reference point to help you start your search.
Othe common locations
There are a few other locations where malware is commonly hidden. Make sure to take a look at these files when trying to find malware:
- Database files such as wp_posts or wp_options
- Javascript files
- Theme files
- Fake plugin files
- Fake .ico files
Scan WordPress for Malware
Identifying malware was the first step. Now that you have located the source of your issues, the next step is to scan your WordPress site and confirm. There are various ways to scan your website, but not all are equally effective. We will go through the three most common ways to scan your website.
Scan using a security plugin
We recommend that you use a security plugin to scan your WordPress website, because security plugins such as MalCare do a thorough job, and can identify malware within minutes.
MalCare makes it very easy for you to scan your site. All you have to do is go to MalCare, install the plugin on your website, and then let the plugin work its magic.
When you log in to your security dashboard, you will find the latest security status of your website.
You can click on the ‘Scan Site’ button to start scanning your website. Once you do, the plugin will conclusively tell you if your website has been infected with malware.
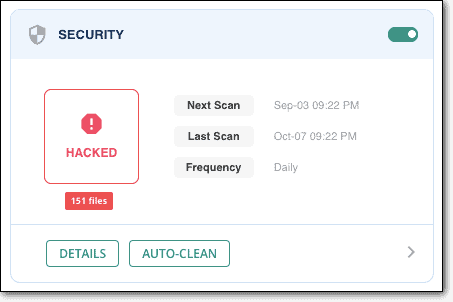
With this information, you can take the next steps to secure your website.
We recommend MalCare for a number of reasons. Most other security plugins use file matching to identify malware. Which means that they basically have a list of issues to look out for. But what happens when there is a new type of malware that is infecting your website? It isn’t on the list, so it is not detected.
MalCare does not scan your website the easy way, instead, it has a sophisticated algorithm that combs through your code to determine if your website is infected.
Scan using online tools
Security plugins are not the only way to scan your website. There are other ways, albeit not as effective. You can use online malware scanners to scan your website quickly, to confirm a hack.
With online scanners
However, it is important to remember that online scanners can only check the files on your website that are publicly visible, and if the malware is hidden in other files, then these scanners won’t catch it.
We recommend that you use these scanners only as of the first layer of the diagnosis and not by themselves. If an online scanner confirms a hack, you can either use a security plugin or hire an expert to do a thorough scan and cleanup of your hacked WordPress website.
With Google Diagnostic Pages
Google offers a range of tools to help you determine if your website is infected. The browsing warning or blacklists are confirmation enough of malware on your website, but there are other tools that can help as well.
You can run your website through Google’s Transparency report, which will tell you if your website has been blacklisted. Or, you can use the Search Console which periodically scans the website. During one of these scans, if it encounters malware, it will flag the issue.
Scan for malware infection manually
The final mode of scanning your website is by conducting the scan manually. We do not recommend this unless you are a security expert. Malware is complex and can hide effectively if you don’t know what you are looking for. Therefore, it is best to rely on experts who have spent thousands of hours building security plugins for this express purpose.
But if you must scan your website manually, here is how you can do it.
With recently modified files
One of the quickest ways to look for malware is by taking a look at the recently modified files on your website. To do this, you can use an FTP client such as File Manager and it will show you the last modified date on each of the files. If you notice any modifications on unusual files, it could be a sign of malware.
However, if you don’t know what you’re looking for it can be an exercise in futility. So if you find yourself wondering what you’re looking for, it is best to rely on a security plugin.
With core WordPress file integrity
Your WordPress core files are what make up the foundation of your website. In order to check if the core files’ integrity is still intact, you will need to download WordPress from WordPress.org and match the files with the ones on your website. Make sure to download the same version that was installed on your website. If you notice any differences, it could be a sign of malware on your website.
How to remove malware from WordPress site easily
If you have confirmed the presence of malware on your website, you have already identified the issue. So you are closer to getting your site back on track.
There are different ways to remove malware from WordPress site, and some are more effective than others. We are going to discuss the two most common ones.
Clean malware from WordPress using a Security Plugin
MalCare is the easiest way to clean malware from the WordPress website. Not only is it fast, but it is extremely effective. We recommend this course of action for anyone who has an infected site because MalCare is thorough, and its intelligent algorithm learns from every hacked site that it cleans. Follow these steps to remove malware from your WordPress website with MalCare.
- Log in to your MalCare dashboard
- Go to the Security section on the dashboard
- Scan your site, to get an updated status of your site
- MalCare will show you the latest status of your website
- Click on the Clean site or ‘Auto clean’ button
- Sit back as MalCare cleans up your website
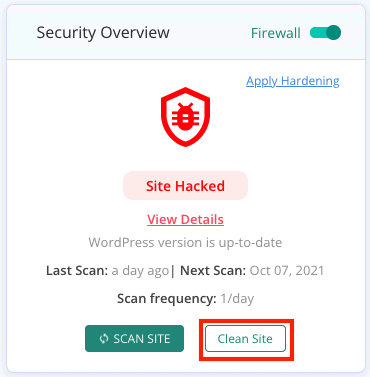
This way, your website is not only rid of the malware, but MalCare also has a powerful firewall that protects your website from any future attacks that may occur.
Remove malware from WordPress manually
Before we get into the nitty-gritty of removing malware from WordPress manually, we must tell you that this course of action is NOT RECOMMENDED. Not only is there a chance of you missing out on malware, but if you accidentally delete a crucial file, it could break your entire site.
Having said that, if you must proceed with a manual clean-up of your WordPress site, this is how you do it. Just follow the steps mentioned below for WordPress malware cleanup manually.
1. Backup your website
First of all, make sure to get a complete backup of your WordPress site before you attempt to clean it up manually so that if anything goes wrong, you can restore your website. It is better to have a hacked site over losing it completely.
2. Download clean versions of WordPress core, themes, and plugins
In order to restore your website, you need uninfected files for your WordPress website. Given that malware could be anywhere on your website, it is best to download the clean installs of your website files from the WordPress repository. Make sure you download the same version as the ones on your website to compare the files and locate any malware.
3. Reinstall WordPress core
Now that you have the clean versions of your website components, it is time to start the actual WordPress malware clean-up process. The first step is to reinstall the core files. We have said this before, but ensuring that you use the same version as before is extremely important, or else your website will not work properly.
You can use cPanel of SFTP to access your WordPress files, and then replace the ‘wp-admin’ and ‘wp-includes’ folders. These folders do not contain any user content, so replacing them is relatively hassle-free. Once you do this, look for malware in the following folders:
- index.php
- wp-config.php
- wp-settings.php
- wp-load.php
- .htaccess
There is no one kind of malware that we can ask you to look for. Therefore, it is important that you ensure that any strange code you come across is malware before deleting it. Additionally, take a look at the ‘wp-uploads’ folder. If you see any PHP files in this folder, delete them, as it is not meant to have any.
4. Clean themes and plugins files
If you have identified malware in particular themes or plugins files, or it appears suspicious to you due to recent modifications, you need to clean these files. Themes and plugins files can be found in the wp-contents folder. You need to go through each of these files one by one and compare them to fresh downloads to find any suspicious code.
Bear in mind, that not all changes in the files are bad. If you have customized any of your extensions, it will reflect as additional code in these files.
Important note: Never use a nulled theme or plugin on your WordPress site. Not only are they riddled with vulnerabilities, they often carry hidden malware.
5. Clean malware from WordPress database tables
In addition to the files, you also have to remove malware from WordPress database tables. For this, you need to use your database admin panel. Once you log in to the admin panel, you need to look for any suspicious content. Check the ‘wp_options’ and ‘wp_posts’ tables specifically. If you want to clean your database tables effectively, you can go through this detailed guide.
Once you locate the table with suspicious content, you need to open the table and manually delete said content. Once you’re done with this, test your website to make sure that it is still functional.
6. Remove all backdoors
You have cleaned your WordPress site now. But unless you remove the cause for malware, there is a strong chance of your WordPress website getting reinfected. To secure your WordPress site from any future attacks, you need to remove all the backdoors.
Backdoors are gaps in the website code that allow hackers to inject malware into your website and gain access to it. You can search for common backdoor keywords or terms such as eval, preg_replace, str_replace, base64_decode, gzinflate, etc. and delete them if you find any.
Important note: The keywords mentioned above can also be used in website code, and may not be a part of malware. If you’re not an expert at clean-ups, it is best to use a security plugin for this purpose.
7. Reupload cleaned files
Once your clean-up is done, you need to reupload these files to your website. This process is very similar to restoring a backup manually, and you can use cPanel or SFTP to do the same.
First, you need to delete the files and tables that you plan on replacing, and then upload the clean versions. Make sure you have your backup in place in case anything goes wrong in this step.
8. Clean the cache
Cache stores versions of your site in order to reduce the requests that go to your website server. But this means that if your site is hacked, the cached version of your website will also have malware. You need to clean up the cache on your website to make sure that your website is completely clean.
9. Verify each plugin and theme
Your themes and plugins could hide vulnerabilities or traces of malware even after a clean-up. So verifying each one of them is important.
To verify your themes and plugins, you need to disable them all. You can do this by renaming your wp-contents folder to anything else. Then, activate them one-by-one and see if your website behaves differently, or if the extension works fine. If everything goes smoothly, your extensions are malware-free.
10. Use a security scanner to confirm
Malware is not predictable, so it is worth confirming that your WordPress site is completely malware-free after cleaning your website manually. Use a security scanner to scan your website thoroughly and determine that there are no traces of malware left on your website.
This step will give you additional confirmation and tell you if your efforts have borne fruit. If the scanner still detects malware, it may be prudent to use a security plugin for clean up.
Important steps to take post WordPress malware clean up
Congratulations! You have successfully cleaned malware from your WordPress site. It is no small feat. But the process isn’t over yet. You need to take some additional measures to secure your website further.
Secure user accounts
After having cleaned up your database and files, you now need to secure all your user accounts. Because, if the malware entered through one of the user accounts, there is a chance your website may get reinfected.
Change all the passwords on your WordPress account, including your hosting panel, database, and FTP passwords. Also, check for any extra or suspicious user accounts that you may not have created. Delete any such suspicious accounts that you may encounter.
Remove malware warnings
When your site is infected, it is flagged by search engines and web hosts alike. Many websites and web hosts use Google’s blacklist too, so it is important to take off the malware warnings on Google. You can do this through the Search Console, which allows you to request a review once your WordPress website is clean from malware infection.
These steps should help you revert most damage. But remember, that malware is not predictable. It can hide anywhere act erratically, so it is always difficult to spot it. The best course of action is to use a security plugin, as it is developed by experts who have researched malware at length.
How did your site get infected with malware?
You may have taken measures to secure your site, and still ended up with malware. This happens because code always has gaps. Your WordPress website is entirely made up of code, so it is important to realize that no website is 100% secure.
This can sound disheartening, but there are ways in which you can secure your website so that even if there are hacks and attacks, you can avoid them or keep the damage to a minimum. But if you are wondering what causes hacks in the first place, here are some common causes:
If you have MalCare installed, it will detect vulnerabilities in advance and alert you. While also securing your website from other issues.
Impact of malware infection on your WordPress site
You already know that malware is bad for your website. But how bad is it exactly? The effect of malware on a website can be far-ranging. Depending on your website, the type of malware, and a few other factors, the presence of malware on your website can very well derail your business operations. These are just some of the consequences of malware that you may expect:
- ‘Deceptive site ahead‘ warning by search engines
- Account suspension by your web host
- Google blacklisting
- Website defacement
- IP blacklisting
- Traffic redirects to spam sites
- Addition of spam pages
- Data breach or loss
Malware is never good news, and the best course of action to follow is to secure your website at the earliest. If you suspect malware, get rid of it as soon as you can, because the situation will get worse the longer malware stays on your website.
How to protect your WordPress site from malware infection in future
If your website has been infected, chances are that it will get reinfected. Hackers tend to exploit backdoors or vulnerabilities on your website, and it becomes easier to hack a website once it has already been hacked. But there are ways in which you can secure your website from future attacks.
Invest in a security plugin
A security solution such as MalCare protects your website from attacks and alerts you of any vulnerabilities in advance. MalCare’s powerful firewall also keeps any unwanted requests at bay, and ensures that your website is completely secured.
Instead of taking action after you detect malware, it is best to proactively secure your website with a complete security solution.
Take frequent backups
We recommend that you take daily backups of your website, and real-time backups for WooCommerce websites. Backups are the hail mary of your website security—if nothing else works, you can always restore your website.
BlogVault offers regular automated backups that are stored on offsite servers, so that if you lose access to your website, you can still restore your backups, and gain access.
Update your website regularly
Developers often spot vulnerabilities in themes, plugins and even WordPress itself. As soon as these vulnerabilities are discovered, they release a patch for these through new updates. Therefore, it is extremely important to update your website regularly. This way, your website remains secure from hackers who exploit recently discovered vulnerabilities.
Scan regularly
Regularly scanning your website helps you identify malware before it causes any damage. If you only scan your website when you suspect malware, then chances are that malware has already started causing problems for you. So it is best to conduct scans daily in order to stay on top of your website security.
Harden your website
WordPress recommends a list of fixes that you can conduct to secure your website further. These fixes are known as WordPress hardening. If you have MalCare installed on your website, you can harden your website with the click of a button. But if you want to harden your website manually, you can go through this guide that explains all the steps in detail.
Conclusion
Congratulations! You have taken the first step towards securing your website. The more you know about malware, the better you can protect your website. We hope this article clarifies all your questions and concerns regarding how to remove malware from WordPress site.
The best thing you can do for your website now is to get a security plugin, which not only protects your website but improves it. MalCare protects over 300,000 websites with its powerful algorithm, intelligent firewall, and thorough scans. But that’s not all, it actively enhances your website performance by offloading its processing to offsite servers and keeping bot attacks at bay.
FAQs
How to remove malware from my WordPress site?
If you suspect malware on your website, these are the steps you should take:
- Scan your website with MalCare—it’s free!
- If you confirm malware, it’s time for a clean up
- Take a backup of your website
- Clean WordPress from malware using a security plugin like MalCare
- Install a firewall on your website
- Change all the passwords
- Remove the malware warnings on Google
How do I check for malware warnings on Google?
Google flags websites with malware on them for its users. It will either throw up a ‘Deceptive Site Ahead’ warning, or blacklist your website from its search engine. Pay attention to user feedback and occasionally visit your website from an incognito window to make sure that there are no warnings attacked to your site.
How do I manually check for malware?
If you wish to check for malware manually, you can do the following:
- Check for recently modified files
- Check WordPress core file integrity
- Check the number of pages on your website
- Check the .htaccess file
How do I protect my WordPress site from malware?
The best way to secure your website is to invest in a security solution. But in addition to that, you can do the following:
- Use strong passwords
- Take frequent backups
- Conduct scans regularly
- Harden your website
- Update everything
- Install SSL
How do I find malicious code in WordPress?
There are three ways in which you can find malicious code on your WordPress website:
- Deep scan with a security plugin
- Scan with online tools
- Scan manually
The post How to Remove Malware from WordPress Site (Malware Cleanup Guide) appeared first on Malcare.
*** This is a Security Bloggers Network syndicated blog from Malcare authored by Preeti. Read the original post at: https://www.malcare.com/blog/how-to-remove-malware-from-wordpress-site/